- Features
- Pricing
- English
- Français
- Deutsch
- Contact us
- Docs
- Login
Over 5,000 organizations work with Upsun, and they can all rely on a foundation of cloud security standards and vital security practices that work seamlessly to protect their personal information and sensitive data at scale.
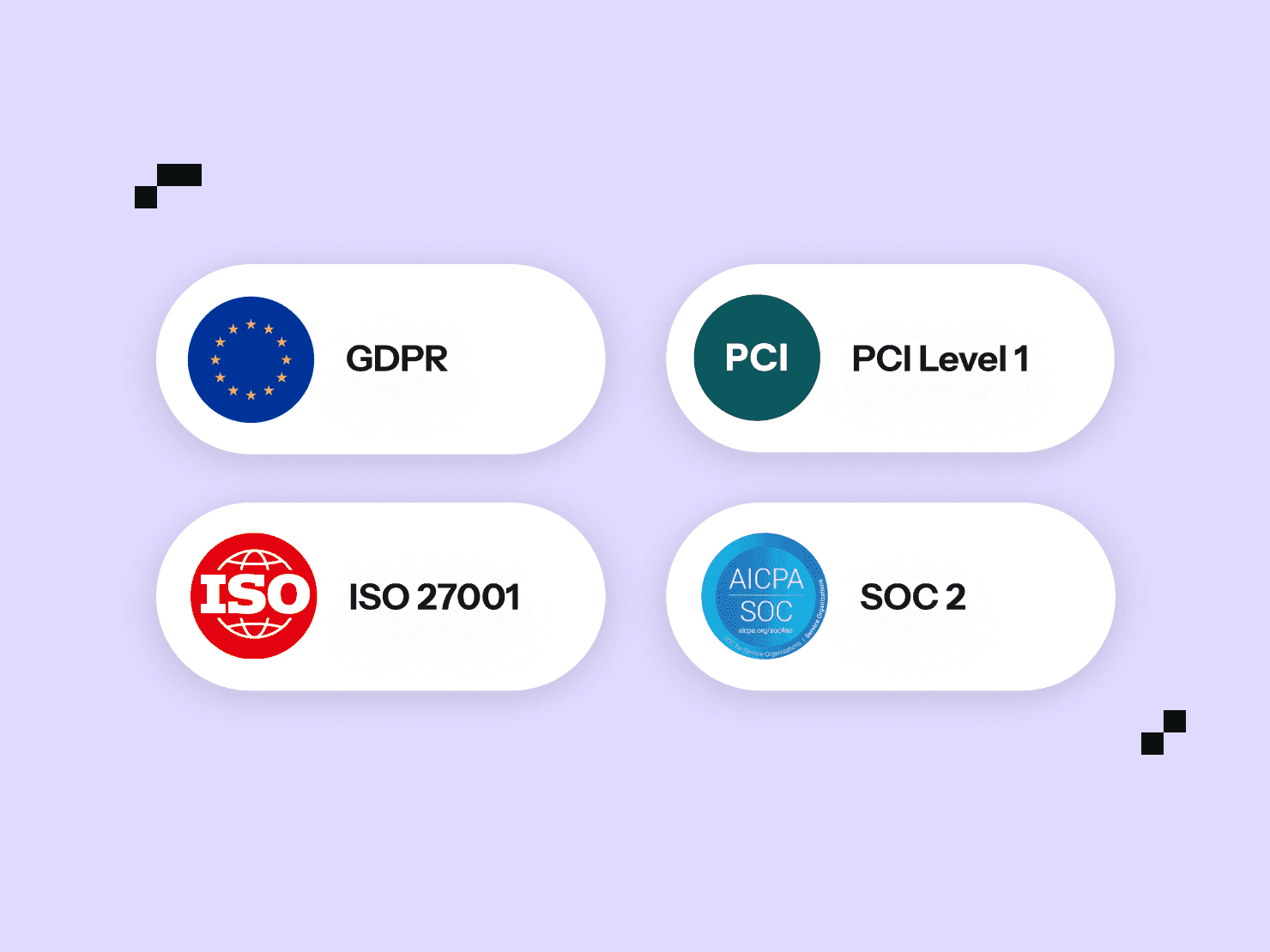
Upsun is compliant with major security, privacy, and information security frameworks. We undergo an annual ISO 27001, SOC 2 Type ΙΙ and PCI DSS Level audit over Security, Privacy, and Availability for our regions hosted on Amazon Web Services, Microsoft Azure, and Google Cloud Platform.
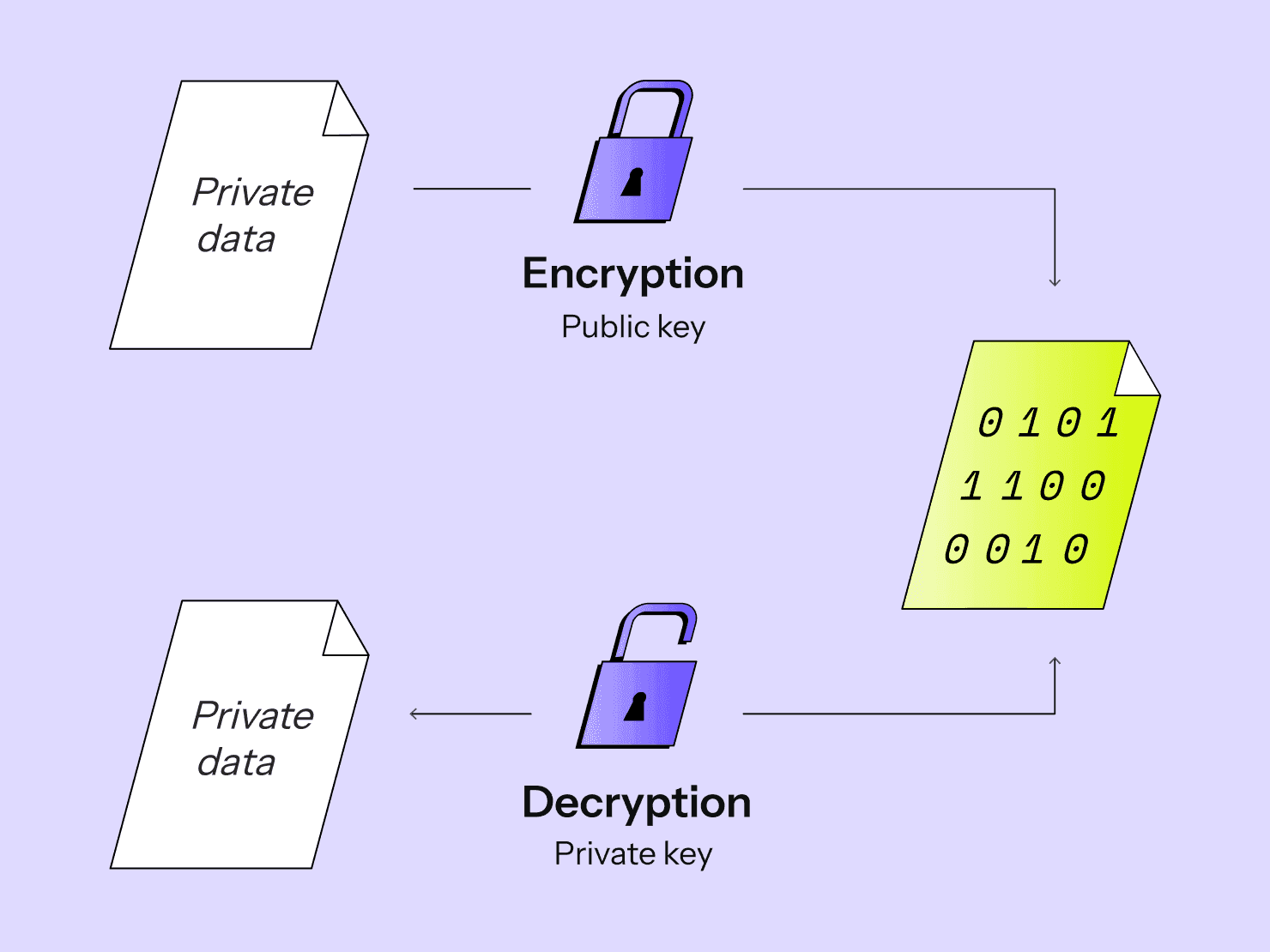
All customer application data in transit is encrypted by default. Plus, we only access data internally for support reasons at the customer’s request, or to fix or prevent an outage. We also maintain a list of Upsun employees with access to customer data, which is reviewed monthly.
Automatic backups can be set up on customer projects to prevent data loss.
We log and monitor access and are alerted when potential threats to our containment model have been discovered.
Upsun regularly updates its container images for the latest security updates from upstream providers. Don't worry, these updates aren't pushed automatically. Instead, the latest available version of every requested container is loaded on each deploy to a given environment. So, after a deployment, you are always guaranteed to run the latest version of a container.
We automate and centralize our access control management and apply the principle of least privilege. Additionally, we audit our own access control lists monthly as a safeguard.
We understand even the slightest outage can have an incredible impact on business. Upsun provides everything you need to keep your applications and websites up and running through the use of our effective automated support system, backups, byte-for-byte clones of production environments, and an optional SLA of up to 99.99% uptime, so you can consistently give your audience the best digital experience possible, without sacrificing security.
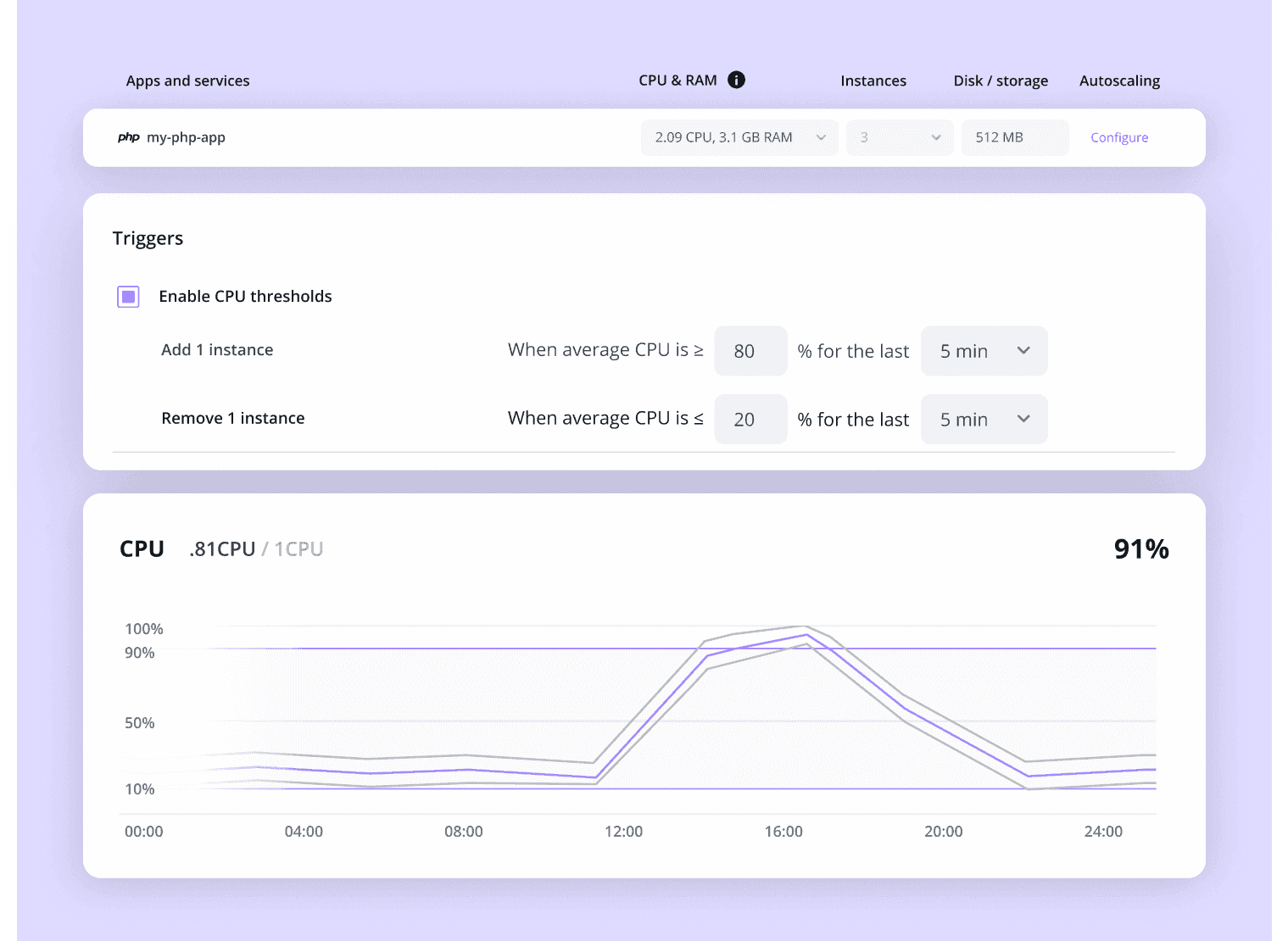
Developers can leverage our built-in reverse proxy cache, TLS encryption on all connections, and optional Distributed Denial of Service prevention. And our orchestration system can automatically increase the resources of your production environment in minutes, so your apps and sites remain available even under the most stressful of traffic surges.
For detailed questions about compliance or assistance completing compliance forms, our team is available to help.
Join our monthly newsletter
Compliant and validated