- Features
- Pricing
- English
- Français
- Deutsch
- Contact us
- Docs
- Login
Team and access management on Upsun provide centralized control over who can access projects, environments, and platform capabilities. Permissions are defined by environment type and enforced at the platform level.
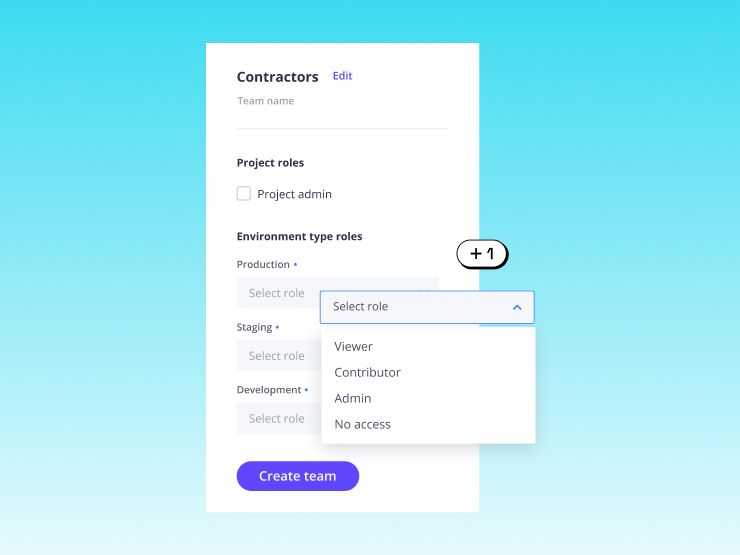
Team and Access Management on Upsun allow teams to:
Upsun uses role-based access control to define what users can do within projects and environments. Roles determine permissions for actions such as deployments, configuration changes, backups, and environment management. Roles can be adjusted at any time to reflect evolving responsibilities.
Users are managed at the organization and project levels in the Console and CLI. Adding a user to a project invites them to the organization automatically, and you can view and adjust their roles centrally. This simplifies access management across multiple applications and teams.
Enforce single sign-on for your domain and use API tokens for automation with the CLI, so teams avoid shared credentials. Access-related activities are logged and viewable in the Console or CLI.
As teams grow, access rights often become inconsistent. Centralized management prevents over-permissioning and reduces security risk.
Manually configuring access across systems is time-consuming and error-prone. Upsun simplifies these workflows through a single control plane.
Without a central view, it is difficult to know who has access to what. Upsun provides clear visibility into user permissions.
Access controls support internal policies and external audit requirements by enforcing consistent permission models.
Least-privilege access reduces the attack surface and limits the impact of compromised credentials.
Platform teams can manage access at scale without maintaining separate identity systems for each application.
A platform team adds new developers and assigns appropriate roles, granting immediate access without manual setup.
An organization restricts access to sensitive projects while allowing broader access to less critical environments.
Security teams review and adjust permissions centrally to ensure compliance with internal policies.
Use Team and Access Management to scale teams securely and efficiently.
Join our monthly newsletter
Compliant and validated